NUVOLLO INC. is a global technology company focused on providing secure private cloud AX as a Service. HOW CAN WE HELP YOU? Reduce cost and increase efficiency by using our cloud infrastructure. Today, most organizations don’t have to spend an absorbent amount of money on purchasing and maintaining IT infrastructure (servers, storage, networks). Nor do they need to employ a large IT team to manage its local setup and day to …
Nuvollo is now a CIRA Member!
Nuvollo is now a CIRA member. CIRA is the Canadian Internet Registration Authority, developing and implementing policies that support Canada’s internet community and ultimately a more secure and better online Canada. We look forward in engaging Nuvollo into a number of CIRA projects.

Any IT issue, we will dig and hold on to the issue right until we get it fixed.
Have you ever encountered a difficult IT issue that appears almost impossible to get resolved? We often get challenged by our clients and users that way. It may be an application being run by an overseas group that somehow lost connectivity and does not want to connect. Or voice quality that badly degrades a few times a week. Or a user account that seems to get locked for no reason …
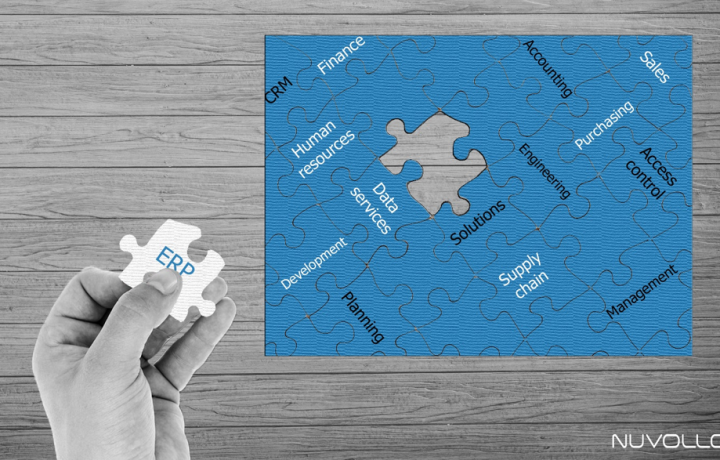
7 Reasons to Adopt ERP Software for Your Business
7 Reasons to Adopt ERP Software for Your Business With the summer, which finally arrived, it’s time to rethink our working methods. We can think about simplifying our tasks and thinking about how to automatizing repetitive tasks, what will give us more time (and of holidays?). The ERP (Enterprise Resource Planning) is a system companies’ resources planning which can bring us on this way.

Connect With Us On Our LinkedIn Page !
You are dynamic, sociable and passionate? In Nuvollo, we foster initiatives, dynamic way of work and skills sharing. If you want to work for a company that is concerned with both satisfaction of its employees and clients… Nuvollo is for you! If you want the opportunity to work with emerging technology and become part of the cloud revolution, send your resume to [email protected], and connect with us on our Linkedin …

TECHTIP#3: How to protect you from spear phishing?
91% OF CYBERATTACKS START WITH A SPEAR-PHISHING EMAIL Spear phishing is an email sent to you that appears to be from a person or company that you know. But it’s not. It’s from a criminal hacker who wants your credit card and bank account numbers, passwords, personal and financial information. Learn how to protect yourself and your company: Verify email addresses to be sure that it’s the real sender …
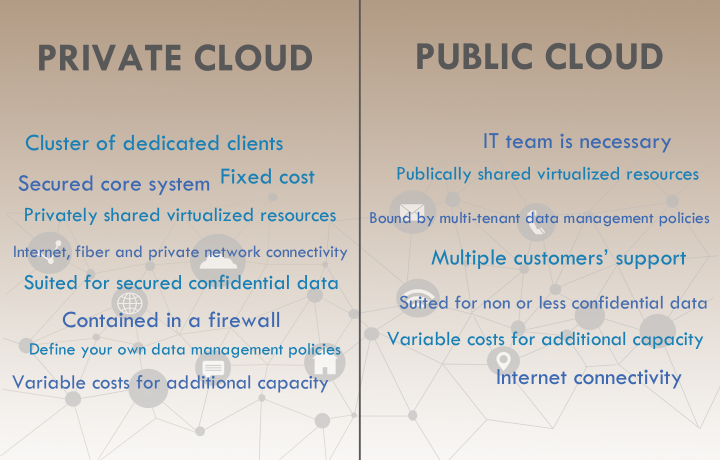
Which cloud is better for your business?
PUBLIC CLOUD A public cloud is based on shared virtualized resources. It’s owned and operated by a service provider. It works with internet connectivity only, so it’s a multiple customers’ support. The first advantage of the public cloud is the speed with which you can deploy IT resources, you can stagger compute power up and down as your business needs in a few minutes. The second, is the ability to …

Follow us on Twitter !
Want to be up-to-date with #cloud, data’s #security, or IT solutions for your #business? Subscribe to our blog! https://t.co/kuOpGvzRbx — Nuvollo (@Nuvollo) June 13, 2017

TECHTIP#2 : How to find good passwords?
Passwords are essential. Indeed, it’s important to protect your network, all its data and your business and/or family. It should meet complex rules to avoid cyberattacks. DOs and DON’Ts to keep your data and accounts safe: DO NOT use a set of same characters/numbers or adjacent on your keyboard: hhhh, 4444, qwerty, 5678. DON’T get inspired by the top 10 passwords of all time (according to Symantec) are: 1. 123456 2. …

Why you should care about your network?
Network run offstage in everyday life, in our business or personal life, and we don’t think about that until something wrong happens. But, what a worst thing than wait in front of a slow screen? So, imagine if your clients wait because of your malfunctioning system… Today, everything works with technology and it grows every time. In addition, it includes more and more business applications in cloud computing: Microsoft Office365 …

TECHTIP#1: Stay safe from cyberattacks
8 behaviors to avoid to stay safe from cyberattacks: Clicking a phishy email Clicking a “cute cats” link on social media that introduce malware Not updating your software and never get the latest security patches Uploading list of social security numbers to Dropbox Using an unmanaged personal device to access company cloud applications Keeping important data on your computer and not on server (servers are usually backed up daily and …

Computing threat in 2017: ransomwares
In the beginning of 2016, a ransomware attack locked computers’ data of the Ottawa’s hospital. To recover the data, the hospital was forced to pay $17.000 US in bitcoins. Not only big organizations are attacked by ransomwares. Indeed, for several years, beginner hackers can easily download virus packs like Trojan Horses, and target individuals, and small & medium sized organizations to infect. In the first quarter of 2016, victims paid more …
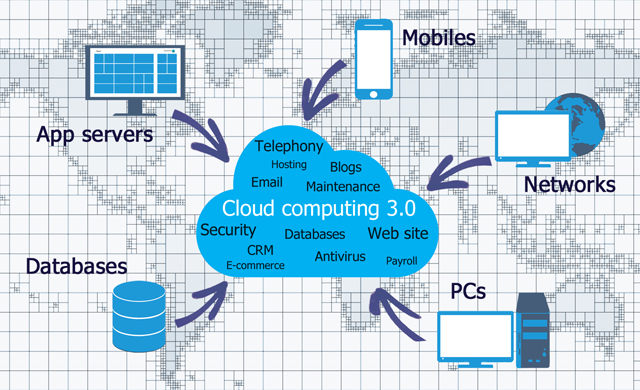
The new wave: cloud computing 3.0
Our CEO Sylvain Boyer is now contributor of the technology section of the French newspaper l’Express Toronto. Come to discover our new press article about cloud computing 3.0 here !

Why disaster recovery is important?
Since a long time, Disaster recovery was neglected but the situation today has changed. Everyone till date has experienced the data loss at least once. It is important to learn the importance of Disaster recovery in order to avoid losses that could have a negative impact on your business. 40% of businesses don’t reopen after a major disaster, such as a fire or a flood. But with a good disaster …

Backup, what is it?
Before talking about backup, it is important to define what data is. The ‘what is backup?’ question seems to be simple, but the answer isn’t so easy as it can take many forms (simple text files, programs, complex information or advanced software). All the files in the company do not have the same importance. But, it needs to be protected as you never know what those files can tell about your …

Cloud computing and business
We all know that digital transformation changes our society and the business world fundamentally. Time today is accelerating and ways to interact with consumers are multiplying. Digitalism is the source of productivity, optimization and new revenue streams, but it also induces new risks. The digital transformation has mutated uses and consequently it redefines the technology market itself. The technology race has never been faster like what we experience today. Obsolescence …

Security and data protection
It is a well-known fact that the security of the cloud infrastructure is perceived as both an advantage and a challenge today. According to IT professionals marketing, in a survey of 300 companies which employee more than 100 employees – 64% of the companies consider cloud to be a more secure alternative to legacy systems. The level of enterprise who trust cloud security is encouraging but it is not that simple. The myth that the Cloud is less secure is rooted in …

