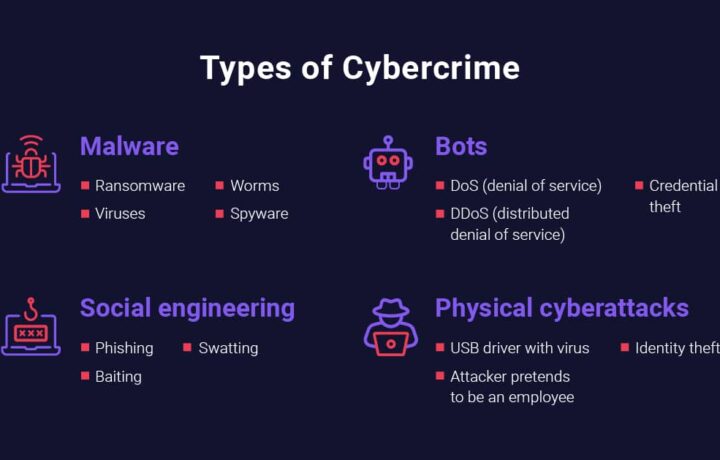
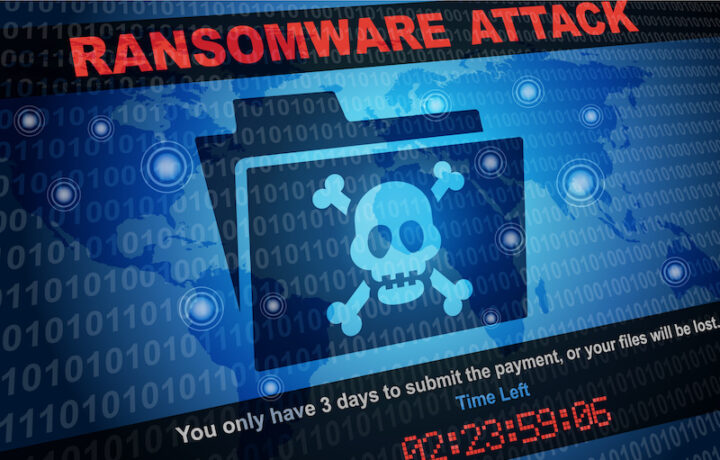
When we think of Ransomware, we don’t think of all the costs of this rapidly growing plague. The global cost of Ransomware payments is in the BILLIONS, an FBI report says that in 2023 approximately $12.5 billion was paid out, and that is just what victims had to pay who reported it! The number is predicted to grow by double digit percentages year over year. What is the actual cost …